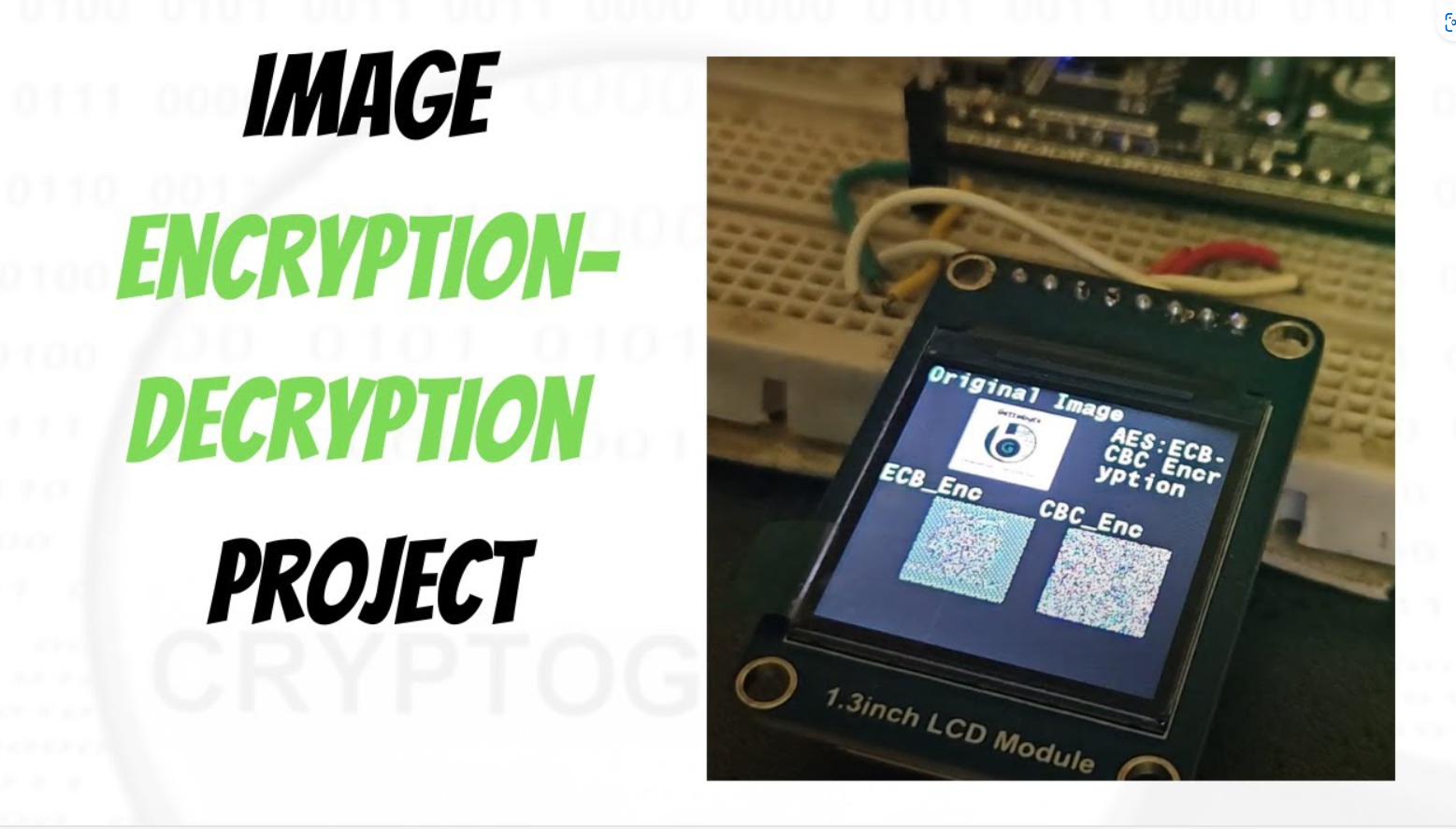
Table of Contents Overview https://gettobyte.com/wp-content/uploads/2023/12/20240211232811.mp4 So, hello guys, welcome back to the gettobyte YouTube channel. The video you have just seen is the encryption-decryption of an image using Microcontrollers. And that’s what we will implement and learn to do in today’s video. We are going to explore, how to use cryptography technology in microcontrollers. Will be doing the hands-on activity for encryption/decryption of data and images using the ElecronicsV2 Development board. Encryption/Decryption is the cryptography concept and what we are going to achieve on doing so is to know how to use cryptography technology through microcontrollers. For doing Encryption/decryption we are using the AES cryptography algorithm, which is supported in the ElecronicsV2 development board through its SHE standard-based CSEc peripheral. For those who are new to the channel and world of cryptography technology, would recommend watching these videos in the following hierarchical order to get an understanding of cryptography and the technical terms that have been stated just now. What is Cryptography How Cryptography is implemented in Microcontrollers Cryptography basic understanding and terminologies DIY Project Statement What i have done here is take an image, which is an original image and convert it into a string of bytes. After that, wrote software to store that string of bytes in the ElecronicsV2 development board and to do encryption through AES cryptography algorithm on the stored data. On successful encryption, those string of bytes are changed to the encrypted format of data and then that encrypted data is processed to print the encrypted image on color LCD Screen. This is just a basic demo on how to use cryptography technology for securing the original data. Here we are printing encrypted image on the LCD Screen, Same way we can send, encrypted image data to other microcontroller via CAN, LIN or any other protocol. Will be doing this activity too in upcoming blogs. Follow this cryptography technology playlist to explore more such demos. Tools needed Now to achieve this, we will be needing some Hardware and Software tools. In Hardware part, we will be needing: 1) ElecronicsV2 Development Board: BuyLink 2) JlinkV9 Debugger: Debugger to program the ElecronicsV2 Board: Buy Link 3) Double Breadboard: 4) ST7789 Color LCD Screen: LCD screen for printing images ElecronicsV2 Development Board JlinkV9 Debugger Double Breadboard ST7789 Color LCD Screen ElecronicsV2 Development Board ElecronicsV2 is a development board built on NXP Semiconductors S32K144 Microcontroller. S32K144 MCU is an automotive Microcontroller based on ARM Cortex M4 Processor and is part of NXP S32 Automotive Microcontroller family. ElecronicsV2 board which is built on S32K144 MCU has a cryptography peripheral present in it, called as CSEc(Cryptography Security Engine). Which is a SHE standard based security sub-system for doing cryptographic operations and establishing secure communication b/w the ECU and the sensors/actuators of the car. We are gonna use CSEc peripheral of S32K144, to do encryption/decryption of data JlinkV9 Debugger JlinkV9 Debugger is a hardware debugging tool, that is used to program and debug ARM cortex-based Microcontroller or Microprocessor. You can buy the JlikV9 from this link. ElecronicsV2 has to be connected to Jlink V9 debugger, so that we can program/debug the board. To know about its connection Double Breadboard Tab Content ST7789 Color LCD Screen ST7789 Color LCD Screen In software we will be needing 1) S32 Design Studio IDE: Which is a Desktop Application for programming S32 Family of microcontroller’s/microprocessor. 2) LCD image converter: Desktop application to convert the image into string of bytes S32 Design Studio IDE LCD image converter S32 Design Studio IDE S32 Design Studio is the IDE that is used for development of Embedded Software Development on S32 family of Microcontrollers. IDE stands for Integrated Development Environment, which is used for doing software development on microcontrollers. ElecronicsV2 board has S32K144 Microcontroller, which is part of NXP Semiconductor S32 family of MCU. Thus, we will be using S32 Design Studio for doing Handson activity with ElecronicsV2 boards, S32 Design Studio: is an Integrated Development Environment to write the microcontroller programs for S32 Automotive Microcontrollers. Install the S32 Design Studio software in your PC and in addition to it user also have to download the Real Time Driver (RTD) package for S32K1 MCU. Refer to this blog for full installation guide of S32 Design Studio step-by-step: Getting Started with S32 Design Studio Part 1 | Gettobyte LCD image converter We will use this software to convert the images into string of bytes. How to use this software is mentioned below: Getting Started Okay so now let’s get started with it, i hope so you guys have gathered all the software/hardware that i have mentioned above and connected all the hardware items. We will at first directly gonna do the practical implementation and then going to dwell deep into it. Now for microcontroller programming on ElecronicsV2, I am making a separate GitHub repo, where all the demo examples and peripherals codes would be committed with time. Clone the repo, into your local PC. Link of the repo: Now in the repo, navigate to: Peripheral Drivers-> CSEc , here you will see different examples related to cryptography technology in ElecronicsV2 Development board.  The CSEc_AES_ENC_CBC_ECB_ST7789, is the project for which demo video is shown to you in the starting of the blog. We are going to execute and understand this project. After cloning the project into your PC, you can see the same folder structure as shown to you at GitHub repo at the path Peripheral_Drivers->CSEc: Now open the S32 Design Studio and we have to open the Project CSEc_AES_ENC_CBC_ECB_ST7789 into it. CSEc_AES_ENC_CBC_ECB_ST7789 is already developed code, so to open it navigate to file->Open Project from File System To know how to open already developed project in S32 Design Studio, refer to this blog: Getting Started with S32 Design Studio Part 1 | Gettobyte. After opening the project, you can see it open in project explorer window of S32 Design Studio. Opening the Cryptography example projects Opening the Cryptography example projects in S32 Design Studio. In this example project you will find
The more realistic you get, the more distinct you become in modern world Gettobyte What is SHE (Security Hardware Extension) Technology? Secure Hardware Extension, short form SHE: is a standard that specifies performing basic cryptography ciphers and managing cryptography keys via automotive Microcontrollers. SHE has been stated as standard in automotive microcontrollers to protect the cryptographic keys from software attacks by hardening them into the memory of the microcontroller and to perform basic symmetric cryptographic ciphers like AES & CMAC for encrypting and decrypting the data. SHE standard is implemented in microcontrollers by having an on-chip extension(peripheral) as a security subsystem which follows, the SHE standard. SHE standard is stated by hersteller-initiative-software (HIS) consortium in April 2009. This consortium was founded in 2004 and consists of members from Audi, BMW, Daimler, Porsche, and Volkswagen to address activities and develop common automotive manufacturing standards. SHE standard states that the peripheral in the Microcontroller should have the following 3 blocks, to implement SHE standard in MCU: Control Logic: Connecting the parts of the CPU to the microcontroller. Storage Area: To keep the cryptographic keys and additional corresponding information. Cryptographic cipher core: a hardware core or module to perform necessary calculations for performing cryptographic ciphers. Automotive Chips, which have SHE peripheral: MPC5646C Freescale MCU’s S32K144 NXP Semiconductor’s MCU Components of SHE Technology SHE Technology Why SHE Technology? Working principal of SHE Technology? USE cases of SHE Technology? How to use SHE Technology? Add Your Heading Text Here
In the new age of autonomous and connected vehicles, cyber-attacks in automotive are happening frequently. Discover in this blog, what technology is used to make our vehicles safe and secure.
Concept of: Cryptography Ciphers: –> Difference between asymmetric and symmetric ciphers. –> Hashing and MACs –> Concept of certificates, digital signatures, and signing 2) Keys in cryptography –> Key storage, Key generation, key derivation, key import, key export, key configuration, key slots shared secret key, master key and etc 3) Attacks in cryptography –> 4) Miscellaneous things: –> Random number generator, Cryptography Ciphers One-way compression functions One-way compression functions: In cryptography, a one-way compression function is a function that transforms two fixed-length inputs into a fixed-length output. One-way compression functions are built from block ciphers. Some methods to turn any normal block cipher into a one-way compression function are Davies–Meyer, Matyas–Meyer–Oseas, Miyaguchi–Preneel (single-block-length compression functions) and MDC-2/Meyer–Schilling, MDC-4, Hirose (double-block-length compression functions). These methods are described in detail further down. Miyaguchi-Preneel Compression function: is used inside SHE standard cryptography A common use of one-way compression functions is inside cryptographic hash functions. Most widely used hash functions, including MD5, SHA-1 (which is deprecated[2]) and SHA-2 use this construction. Using a block cipher to build the one-way compression function for a hash function is usually somewhat slower than using a specially designed one-way compression function in the hash function. This is because all known secure constructions do the key scheduling for each block of the message. Black, Cochran and Shrimpton have shown that it is impossible to construct a one-way compression function that makes only one call to a block cipher with a fixed key.[6] In practice reasonable speeds are achieved provided the key scheduling of the selected block cipher is not a too heavy operation. But, in some cases it is easier because a single implementation of a block cipher can be used for both a block cipher and a hash function. It can also save code space in very tiny embedded systems like for instance smart cards or nodes in cars or other machines A compression function mixes two fixed length inputs and produces a single fixed length output of the same size as one of the inputs. This can also be seen as that the compression function transforms one large fixed-length input into a shorter, fixed-length output. 2) Block Cipher: Block ciphers take (like one-way compression functions) two fixed size inputs (the key and the plaintext) and return one single output (the ciphertext) which is the same size as the input plaintext. modern block ciphers are only partially one-way. That is, given a plaintext and a ciphertext it is infeasible to find a key that encrypts the plaintext to the ciphertext. But, given a ciphertext and a key a matching plaintext can be found simply by using the block cipher’s decryption function. Thus, to turn a block cipher into a one-way compression function some extra operations have to be added. Some methods to turn any normal block cipher into a one-way compression function are Davies–Meyer, Matyas–Meyer–Oseas, Miyaguchi–Preneel (single-block-length compression functions) and MDC-2, MDC-4, Hirose (double-block-length compressions functions. Stream Cipher: AES: ECB mode: CBC mode: MAC generation/verification: Compression Function Cryptographic Keys Types of keys in cryptography: What Is Secret Key Cryptography? A Complete Guide – Helenix Secret Key: the key which is used in symmetric ciphers is a called as secret key. As this is single key which can be used for both encryption/decryptions, thus it is called as secret key. Private key: private key is used in asymmetric key cryptography, where there are 2 different keys for encryption and decryption. Key Usage flags: Different keys are used for different features and specs. So, there are concept of flags through which we can specify which key is to be used for what purpose and its usage limitation. Broadly there are x number of fields in Key usage: Key derivation: A Key derivation function (KDF) is a basic and essential component of cryptographic systems: Its goal is to take a source of initial keying material, usually containing some good amount of randomness, but not distributed uniformly or for which an attacker has some partial knowledge and derive from it one or more cryptographically strong secret keys. There are many forms of KDF’s, and not all functions used as KDF are explicitly named as KDF’s. For instance, the KDF of TLS is simply called “the PRF” for Pseudo-Random-Functions, which is a much more generic term Some KDF’s have input limitations, some have output limitations and not all KDF’s have the same configuration parameters. The base construction of a KDF is: input: a binary encoded secret or key other information to derive a specific key (optional) output size (if configurable) output: a derived key or derived keying material. Furthermore, there are many different parameters possible: a salt work factor (for PBKDF’s) memory usage (for PBKDF’s) parallelism (for PBKDF’s) Cryptography Miscellenous terms Pseudorandom Function Family(PRF):
Table of Contents What is Cryptography Cryptography is a branch of science used to secure communication between two electronic devices, such as cars sending data to one another or an ECU within a car sending data to another ECU. This technology is essential for ensuring the privacy and integrity of data transmission, allowing for secure communication between two parties. How does Cryptography secure the communication? When a sender transmits the original data, known as plaintext, cryptography algorithms are applied to the data to ensure secure transmission. These algorithms are designed to protect the data from unauthorized access, ensuring that only the intended recipient can access the information. By using cryptography algorithms, the data is transformed into an unreadable format, making it virtually impossible for anyone other than the intended recipient to access the data. So as to make that data into encrypted form i.e., in unreadable format. This process is called encryption and unreadable data is called ciphertext. The receiver now receives the ciphertext, which is different from its original message. If an intruder were to gain access to the data during its transmission from sender to receiver, they would not be able to comprehend the actual data as it is encrypted into an unreadable format. This means that the receiver would also be unable to understand the received data, so they must convert it back into its original form, known as plaintext, through decryption. The decryption is also performed using same crypto algorithm which is used at the time of encryption. So, this is how a secure communication is done b/w sender and receiver using cryptography. This is the concept of Encryption & Decrytion. What are Keys in Cryptography? Now one thing to point on this thing is that, if receiver can decrypt the data using crypto algorithm, then some hacker or 3rd person can also do the same. Well, that is not the case, because of concept of keys in cryptography. “Keys are the random string of bytes” which are used during the encryption-decryption by the crypto algorithms to transform the Original Data into Unreadable format & Vica versa. Only the sender and receiver have access to the keys, so only they can encrypt and decrypt the data. However, if someone else were to gain access to these keys, they would be able to access the original data. If the keys were to be exposed, anyone would be able to encrypt and decrypt the data, thus compromising the security of the system. Thus, in cryptography Key Managment, Key Storage, Key Derivation & whole concept of Keys are very important in cryptography. (Would be writing more about crypto keys.) What are Crypto Algorithms?? To give you an idea about crypto algorithms, these are complex & heavy mathematics calculations which uses mathematics concepts like algebraic theory, probability, statistics, discrete math, algebraic geometry, complex analysis, number theory, algorithms, binary numbers, prime factorization, to manipulate the original data. These Crypto Algorithms need mainly 2 inputs: Input data and the Keys. In the case of Encryption Input data would be Plaintext and in the case of decryption Input data would be Ciphertext. Keys would always be used, in either of the case and thus protecting the keys is very crucial part of cryptography. As losing the keys means exposing the original data to would. Crypto Algorithms are also called as ciphers. Some examples: RSA, AES, DES, ECDSA, hashing, CMAC and etc. These algorithms are being categorized in terms of number of bytes of input data and how the keys are used on the input data, as symmetric and asymmetric algorithms. (Would be writing more about and in-depth about crypto algorithms). Implementation of Crypto Algorithms To perform these mathematical concepts, Crypto Algorithms need a heavy amount of processing. We all know, in our web browsers, emails and WhatsApp chats our messages are encrypted and decrypted over the web servers to protect our data. But how does this thing happen in microcontroller level??? So, in MCU/MPU cryptography can be implemented by 2 ways: First by, implementing the crypto-algo through software, in which all mathematical calculations and processing is done on the main CPU only like in the case of Arduino which has dedicated libraries for many crypto Algorithms, for implementing cryptography in Arduino and low-end microcontrollers/applications. But this way the power and time of main CPU is taken very much. Crypto Algorithms takes a heavy amount of processing to perform calculations which takes up a good amount of CPU time & power. In the case of time-critical applications like that Automotive, performing calculations of crypto algorithms & running application code at the same time can be very time-consuming, even a delay of milliseconds(ms) and microseconds(us) can lead to life-threatening for automotive applications. Second, there has to be a certain hardware subsystem (dedicated CPU basically), specially for cryptographic algorithms to achieve the cryptography in fast and efficient way. To Conclude Automotive has revolutionized from traditional times, now there is so much of Automation and Autonomous features like Vehicle-to-Vehicle Connectivity, ADAS, Self-Driving cars and etc. Thus, concerns of safety and cryptography has risen up in automotive.