Table of Contents
Overview
In Today’s blog, we are going to dig into how cryptography is implemented in microcontrollers/microprocessors for Automotive applications. The automotive industry is at its prime then ever and with the market need for autonomous and ADAS technologies in the vehicle, almost every electronic/electrical subsystem of car nowadays is connected to wireless communications. These advancements are fascinating and good to experience, but on the other hand, it has led to the hacking of these sub-systems and an increase in accidents in the automobile industry by cyber-attacks. Since the introduction of wireless communication in automotive industry, cyber-attacks in automotive industry have put the question on safety and security of passengers and driver via automotive vehicles. Thus, the need to secure automotive vehicles has increased more than ever. Here comes the need of cryptography, now days cryptography is being implemented on running vehicles by integrating Cryptography Technology into the electrical/electronic parts of the vehicle.
So, welcome back to the Gettobyte Cryptography Technical learning series of blogs. In the last blog, we get to know about what cryptography is and how it secures communication.
Why Cryptography?

The automotive and Internet of Things market is rapidly advancing towards the age of autonomous driving and connected vehicles. Various sub-systems of cars are now being connected/monitored/ analyzed wirelessly like Smart Battery Management Systems, Infotainment, Wireless Keys, and Wireless communication within cars to off-load use of wires.
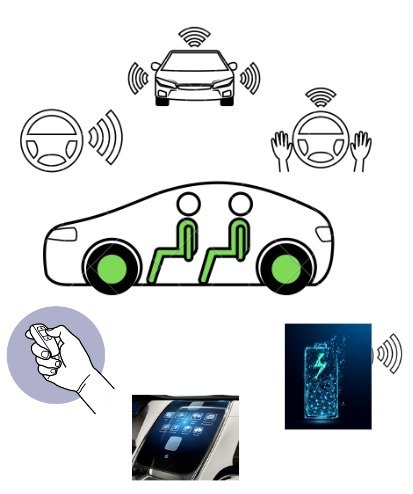
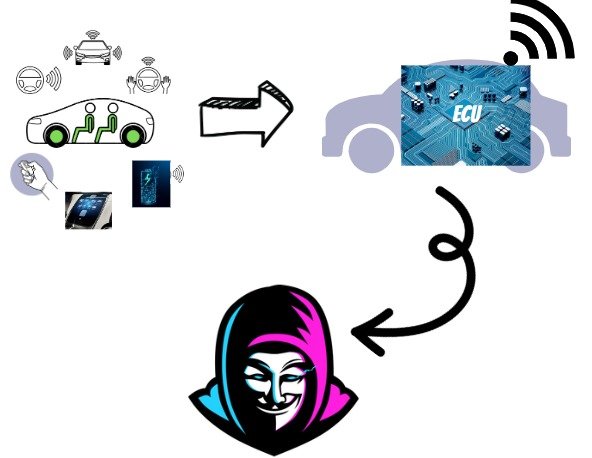
These technological advances require automotive systems, (to be precise ECUs) to be connected to the internet and other communication media to a greater extent than ever. As a result, automotive electronic sub-systems are becoming more susceptible to hacking and gaining unauthorized access to vehicle data or control systems.
To prevent unauthorized access every part of the automotive electronic system needs to be secured, such as:
–> Small microcontroller managing small tasks.
–> To larger gateway processors controlling complex systems.
–> And even application software to store data in memory.

All of these automotive systems are important to the safety/security of the driver and passenger of a vehicle.
Thus Embedded security modules and cryptographic engines in the microcontrollers/microprocessors provide efficient tools for ensuring automotive safety and security by enabling secure information exchange and data authenticity/integrity.
How is cryptography implemented in Automotive?
Now question comes to how cryptography is implemented in the embedded world. Well, to use cryptography in micro-controller/micro-processor there is the concept of security-subsystems in Integrated circuits.
What is a Security Sub-system?
Security Sub-systems are dedicated sub-systems within an IC through which we can perform cryptographic operations in a microcontroller and protect cryptographic keys from software attacks.
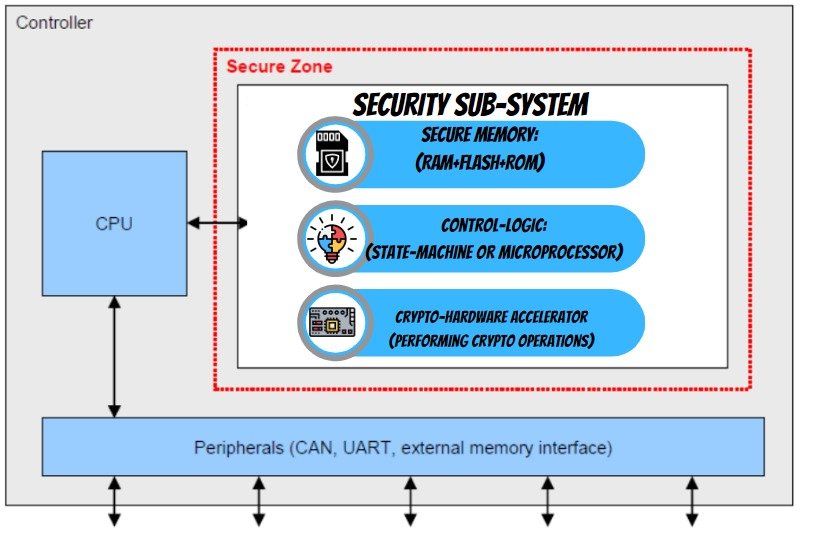
And this security sub-system is based on 2 standards:
- –>SHE (Secure Hardware Extension)
- –>HSM (Hardware Security Subsystem)
What is SHE (Secure Hardware Extension)?
Secure Hardware Extension, short form SHE: is a standard that specifies performing basic cryptography ciphers and managing cryptography keys via automotive Microcontrollers. She has been stated as standard in automotive microcontrollers to protect the cryptographic keys from software attacks by hardening them into the safe memory of the security-subsystem and to perform basic symmetric cryptographic ciphers like AES & CMAC for encrypting and decrypting the data. SHE standard is implemented in microcontrollers by having an on-chip extension(peripheral) as a security subsystem which follows, the SHE standard.

SHE standard was stated by the hersteller-initiative-software (HIS) consortium in April 2009. This consortium was founded in 2004 and consists of members from Audi, BMW, Daimler, Porsche, and Volkswagen to address activities and develop common automotive manufacturing standards. SHE was implemented as a state machine with cryptographic functions based on the Advanced Encryption Standard (AES) algorithm and included enough NVM to store the required keys and counters. To know more in-depth about SHE standard and its different, features and specs, refer to this blog.
What is HSM(Hardware Security Module)?
Within a few years, the automotive industry recognized that higher levels of security were required in certain automotive applications.
Thus, the Hardware Security Module (HSM) is a standard that is built upon the legacy SHE standard but added an ARM CPU to manage HSM operations. Many advanced Crypto operations were added to HSM standards like Asymmetric crypto ciphers (ECC, RSA), Digital Signatures and certificates (ECDSA & EdDSA), Hashing algorithms (SHA & MD5), Key derivation functions, etc.

So, the Microcontrollers which will be following HSM standards would have one additional core/CPU in it, which will be dedicated to performing crypto operations. This HSM Core would communicate with the main Application core via some hardware interface. This means that in an SoC there would be one dedicated core that will be acting as a security sub-system for performing cryptographic operations and providing safety/security capabilities for automotive applications.

HSM Standard is stated by EVITA Workgroup, which stands for E-safety vehicle intrusion protected applications. This Workgroup was started in July 2008 till December 2011. The objective of this group is to design, verify, and prototype an architecture for automotive on-board networks where security-relevant components are protected against tampering and sensitive data are protected when transferred inside a vehicle.
EVITA can be considered a competitor to the TPM 2.0 Automotive Thin Profile. However, EVITA does not offer remote attestation and cannot measure the state of the ECU against a set of pre-stored measurements. However, EVITA offers a comparable, flexible approach, allowing the hardware implementation to be varied to ensure cost-effective protection of the in-vehicle network.
EVITA Group proposes 3 variants in HSM
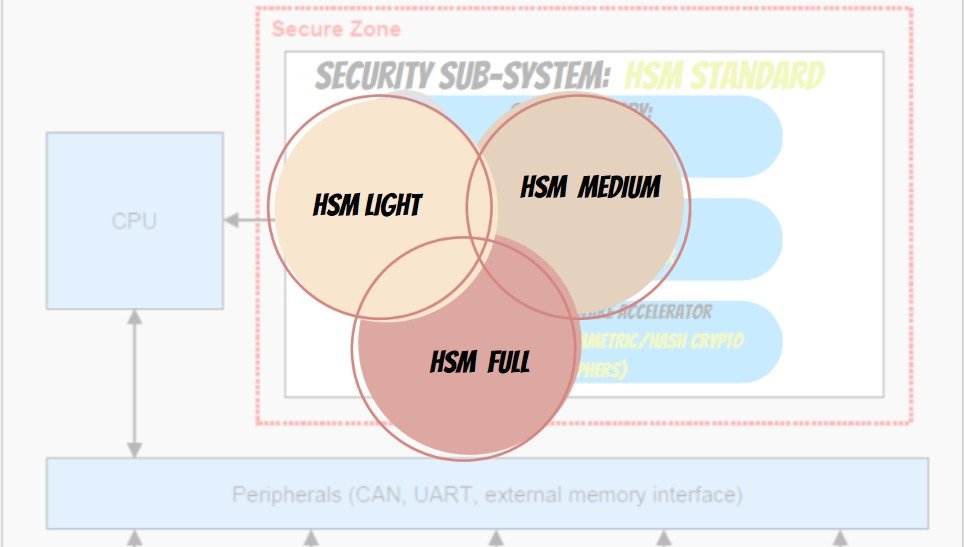
Based upon different crypto operations and features supported by them, as specified in this table. To know more in-depth about HSM and its different variants, features, and specs, refer to this blog.

So, to conclude for performing Cryptography in automotive application, there should be security sub-systems in the microcontrollers/microprocess based on above 2 standards. These standards are mandatory in automotive industry and being acknowledged/followed by almost all companies in automotive/semiconductor Industry.
Cryptography Usecases
Broadly stating there are 3 levels of security functionality and performance in automotive:
- –>V2X/V2I messages (high-speed asymmetric encryption and key storage)
- –>On-board communication between ECUs (low-speed asymmetric cryptography, high-speed symmetric encryption, key storage and dynamic communication: 2-way communication requirements)
- –>On-board communication to Sensors and Actuators (symmetric encryption and key storage; static communication: One-way communication requirements).
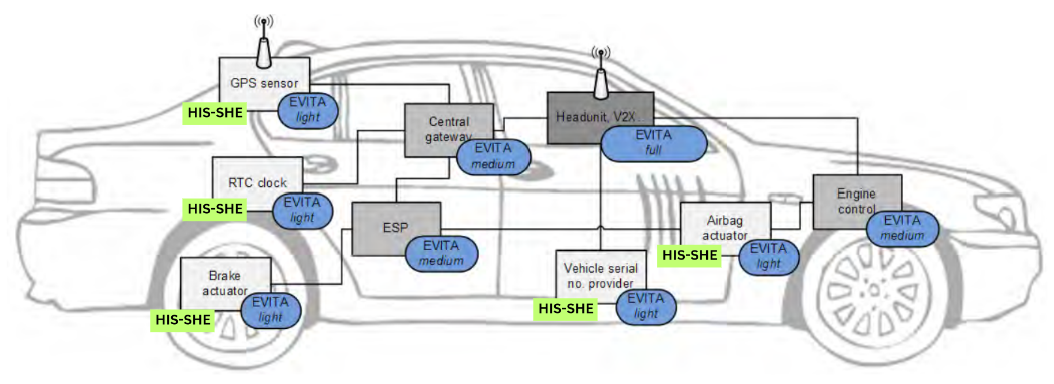
As you can see in the above image:
Cryptography in ElecronicsV2 Board
Now, let us delve into the question of how cryptography can be utilized in automotive applications, enabling us to engage in do-it-yourself (DIY) hands-on and practical projects. The key lies in incorporating a microcontroller equipped with a security sub-system or peripheral, capable of executing cryptographic operations while meeting the specific requirements of the automotive industry.
By integrating such a microcontroller, we can harness the power of cryptography to enhance the security and functionality of automotive systems. This enables us to embark on exciting DIY projects, where we can explore the practical applications of cryptography within the automotive realm.
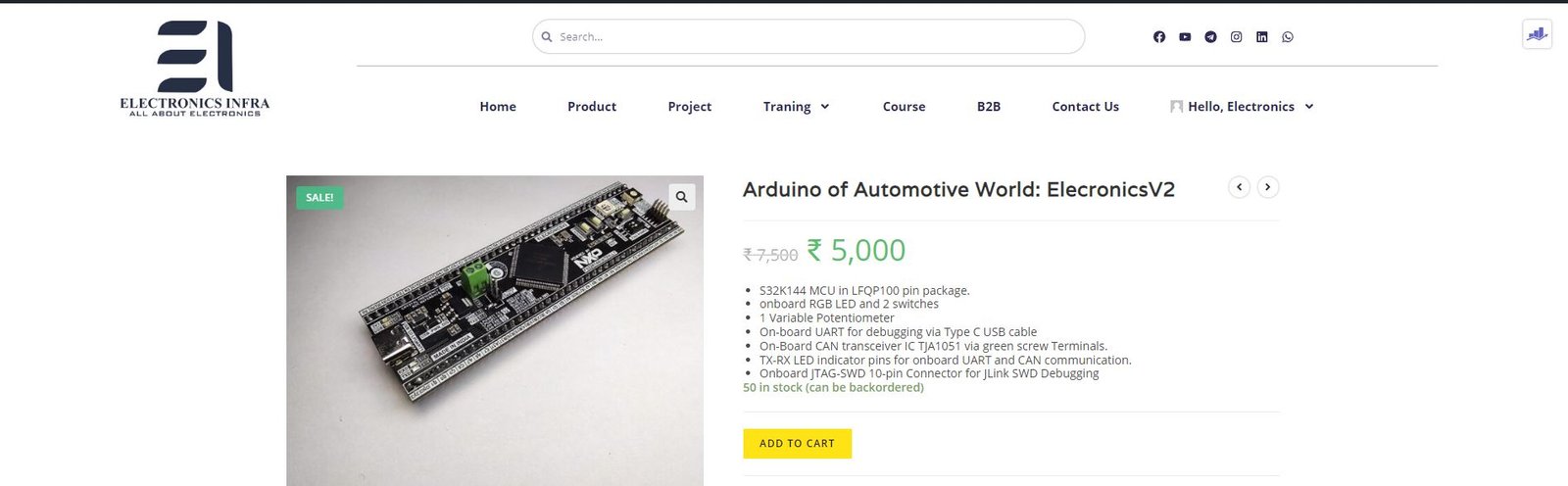
Here comes, the ElecronicsV2 Board, which is built on S32K144 Microcontroller. S32K144 is an automotive microcontroller with safety complaint ISO26262 up to ASIL-B.
And S32K144 has a very interesting and important safety peripheral present in it: CSEc. Which is a security sub-system for doing cryptographic operations and establishing secure communication b/w the ECU and the sensors/actuators of the car.
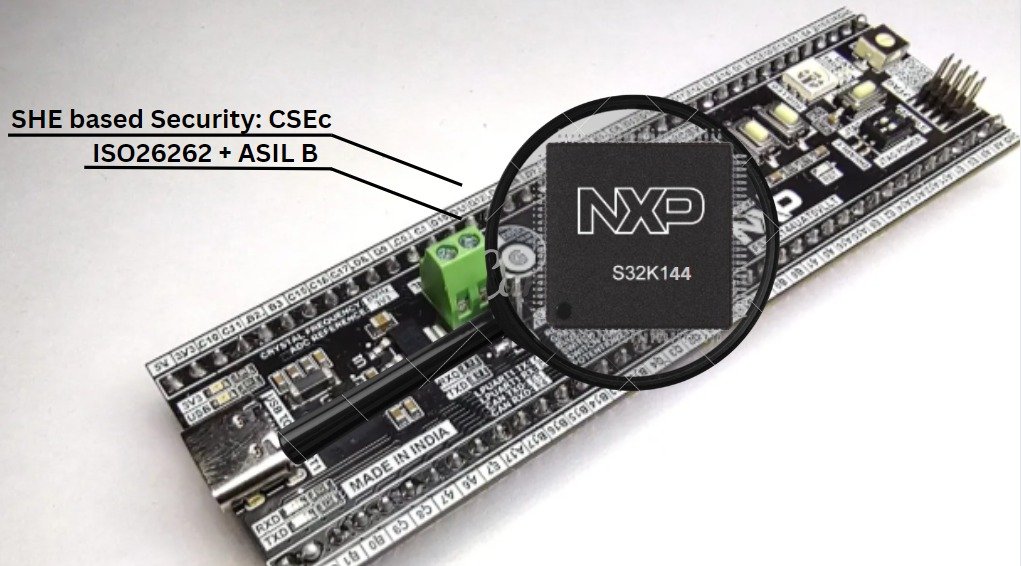
CSEc peripheral in S32K144 is based on the SHE standard security sub-system. That means using the CSEc peripheral present in S32K144 MCU, we can perform symmetric crypto operations and secure up to 17 user keys. To narrow it down, the CSEc peripheral of S32K144 has the following features:


Buy the ElecronicsV2
Microcontroller's/Microprocessor supporting cryptography
MCU/MPU supporting EVITA Full HSM:
- –> NXP Semiconductors S32K3 series of Automotive MCU based on ARM Architecture based processors.
- –> STMicroelectronics SPC58H series of Automotive MCU’s based on Power Architecture based processors.
- –> Infineon Technologies Aurix TC3xx series of Automotive MCU’s based on TriCore Processor Architecture.
- –> Renesas Semiconductor’s R-Car Series Automotive System on Chips based on ARM processor Architecture.
MCU/MPU supporting EVITA Medium HSM:
MCU/MPU supporting EVITA Light HSM/SHE standard:
Vehicles supporting the cryptography
Examples of New Vehicles Using Cybersecurity Measures
- Audi E-Tron GT: uses a secure boot process and a security gateway to prevent unauthorized access to the vehicle’s electronic control units.
- Ford Escape: features cybersecurity measures such as secure software updates, intrusion detection, and data encryption to protect against cyber threats.
- Tesla Model 3: employs a state-of-the-art security architecture that includes encryption of all data communications, two-factor authentication, and over-the-air software updates to quickly address security vulnerabilities.
Author
More Blogs on ElecronicsV2 Board
Now lets come down to question, how we can use cryptography for automotive applications, so that we can do DIY hands-on and practical projects with it. Answer to that is to have the microcontroller which has security sub-system/peripheral in it to perform cryptographic operations, with automotive capabilities.
More Blogs on Crytography